Small but Risky: What are the risks of using Malicious USBs?
USB devices are the best means of storing and transferring sensitive data from one device to another. Compatibility, Speed, and Durability are the 3 factors that make USB the best device to store & transfer data
But, do you know Removable media devices such as USBs or Pen drives continue to be a rising security concern for various industries? Just like a small tablet helps to cure the entire body. Likewise, a small USB is enough to create wreaking havoc in your digital life. So, don’t fall for the small device, rather stay safe from the big explosion it can perform.
Nowadays, people have at least one USB device to store sensitive data or transfer it to another device. On the other side, sometimes; you may bring that USB device to your office to revive the old memories you’ve lived so far. As soon as you insert USB into the trusted machines, you are safe! However, plugging them into an unknown device can prove disastrous unless you use Total Security Software that comes with advanced USB threat protection.
In the so-called safe digital world, no one and no device is safe & human curiosity is something that lures the interest of hackers.
Inserting an unknown USB in your PC/laptop can damage your device and take your sensitive data in a matter of seconds. So, you better be careful while inserting an unknown USB device into your computer, no matter if the pen drive belongs to an employee or a client.
As you all know that “Unknown things are always suspicious.”
And, if you think that you and your device are safe in this digital world, it’s time to “Think AGAIN!”
How do malicious USB attacks work?
A USB attack takes place in the following steps.
Firstly, an attacker keeps an unknown USB device with a malicious code near the victim. The code is then executed if the victim plugs the device into the system. But, if the victim has Total Security Software installed in his/her system, the risk is greatly reduced!
This is because Total Security detects unusual behavior and stops the USB attack!
What are the dangers of unknown USB drives?
A malicious USB device allows intruders to steal the passwords stored on your device, gain unauthorized access to your sensitive data and information, or gain proper control of your device. Talking about the worst scenario, a USB attack can also disrupt the whole device so that you can no longer use it in the future.
Malicious USBs can also be an effective way for cybercriminals to gain complete access to a computer, or server, or to disrupt an organization’s complete network. A hacker only needs a person who’ll plug the unknown USB device into the computer.
So, you better be careful as you can be the NEXT victim of a USB attack!
6 Tips to Stay Protected from Rising USB Attacks!
Here’re some tips to protect your sensitive data from the lurking dangers of unknown USB Devices.
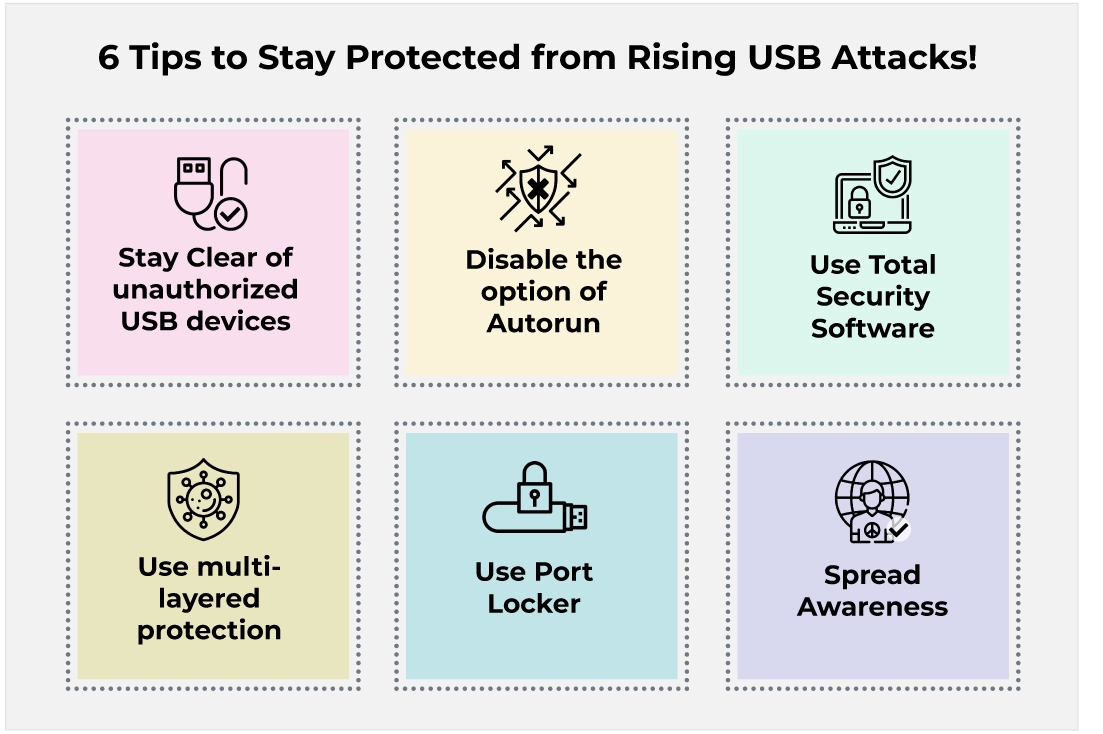
- Stay Clear of unauthorized USB devices
Connecting your own USB device to your computer is the best choice if you want to stay away from rising cyber-attacks. Don’t plug in a device that is unknown as it might bring Malware into your system. Also, if you want to do so, it’s always better to perform a quick Scan for any possible viruses.
- Disable the option of Autorun
Have you enabled the Autorun feature for Windows on your computer? It’s always better to disable the Autorun feature by going into your computer settings. Doing this will give you more control over your computer and will prevent the automatic running of the USB.
- Use Total Security Software
You can stay clear of USB attacks if you have Total Security installed in your system as it provides you with advanced USB protection. Not only this, but it also comes with the option of advanced parental control that allows you to keep a check on your kid’s online activities.
- Use multi-layered protection
It’s always better to use multi-layered protection as USB attacks have the power to destroy your existing firewall. So, in addition to investing in Antivirus, invest in a reliable backup system to protect your business from any kind of online danger.
- Use Port Locker
Port Locker is the best Data leakage prevention software. With the help of this, you can block single or multiple ports and stop the entry of USB in your system. When any unauthorized action is performed on the port that you’ve blocked, you’ll receive an alert message. Install now if you want to keep your sensitive data safe and secure.
- Spread Awareness
Awareness is the key! Organizations need to educate their employees about the rising USB attacks & teach them not to insert any unknown device in the systems as it may contain malicious codes that may put the organization’s sensitive data at risk.
With these suitable protocols in place, you can ensure that your sensitive data remains safe & secure from USB attacks!