
Understanding rising Phishing Attacks and 9 Ways to avoid falling victim
Over a couple of difficult years, we have seen that businesses worldwide have been forced to become tech-savvy and adopt cutting-edge technologies – and do you know that cybercriminals are furious to catch up with the latest victims? According to the “IBM 2022 Cost of Data Breach Report”, stolen or compromised credentials remain the topmost cause of Data Breaches. The report also reflects some other facts such as:
- Phishing is the second most common cause of Data Breaches at 16%, which costs around $4.9 Million.
- Phishing has the longest lifecycle as it takes 243 days to identify the breach.
But, despite the threat that Phishing poses to businesses today, only 1 in 5 organizations deploy Phishing awareness training to their employees per year. Also, many businesses fail to recognize the importance of Total Security Software in their organizations. Before we get into ways to avoid Phishing attacks, it’s always a wise idea to know, “What Phishing is?”
What is Phishing?
Phishing attacks are a type of cyber-attack designed to persuade people to hand over sensitive information such as passwords, OTPs, and other financial information related to Debit & Credit Cards. No matter the information captured, the hacker’s end goal is to steal all your money! These attacks are typically carried out through fraudulent emails, messages, or websites that impersonate legitimate organizations or individuals
According to APWG reports, it was observed that the total phishing attacks were the highest in 2022. With more than 12.7 lacs attacks in the third quarter, this represents the worst-case scenario.
The statistics mentioned above are a perfect example of how attackers are becoming three times more sophisticated and successful in planning Phishing attacks. This is especially true in the absence of Antivirus Software.
Have you watched the latest Netflix Original Series, Jamtara?
Nowadays, no one is safe. Everyone receives a call from an unknown person at least once, twice, or thrice a day. Well, how many of you know that the unknown call was from “Jamtara,” a famous district of Jharkhand? Not only is it a Jharkhand district, but Jamtara is also a Netflix Original Series with a catchy tagline “Sabka Number Ayega.” This seems very appropriate, considering the number of rising phishing scams & gripping the country.
Jamtara follows the complexity of cyber criminals and how they use them to scam unsuspecting individuals by sending links, OTPs, and executing other malicious plans to loot people’s hard-earned money. Imitating a different voice, and offering to update your KYC details or apply for a credit card are some popular scamming techniques used by these millennials.
Unfortunately, Jharkhand isn’t the only hot spot for cybercriminals to operate. Haryana, UP, Rajasthan, and Gujarat are also cybercrime hubs.
Human Behavior is what makes Phishing attacks successful.
The problem behind the rising attacks isn’t the lack of Total Security Software designed to detect, prevent, and eliminate threats – but, it’s the human response that makes these attacks successful.
The bad guys are sneaky, sophisticated, and technically advanced but they need humans to behave in a way to implement a successful Phishing attack. A single OTP is what a hacker needs to steal your years of saved money.
So, how careful are you while answering a call from an unknown number? If you answer a call received from an unknown person, it’s essential to verify the caller’s identity before sharing personal information or engaging in sensitive conversations. Ask for their name, organization, and the call purpose.
If you’re uncertain about the legitimacy of a call, it’s advisable to end the conversation and independently verify the caller’s identity through official channels. This is before providing sensitive information.
9 Best Ways to Avoid Phishing Scams!

To avoid falling victim to the rising Phishing Scams, here are 9 Best Ways:
- Be cautious with emails and messages
Phishing attacks often come through emails, text messages, or instant messages. Be wary of messages from unknown senders or those with suspicious content. For example, urgent requests for personal information or offers that seem too blatant to be true.
It is blatantly obvious that certain emails are so deceptive that it becomes difficult to differentiate them from legitimate ones. You should know some best practices to avoid spam emails and messages. Some of the best practices are:
In contrast to other scenarios, the unexpected always brings the worst when it comes to clicking on deals that seem too good to be true! So, be careful.
- Avoid clicking on suspicious links
Phishing has existed for as long as the web has been, and so are cybercriminals. Phishing emails often contain links to malicious websites. Hover your mouse over the link (without clicking) to see the actual URL. If it looks suspicious or doesn’t match the expected destination, don’t click on it. Instead, manually type the URL into your browser or use a trusted bookmark.
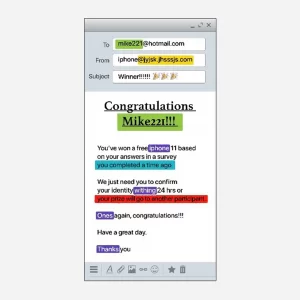
The above image is a perfect example of a Phishing email in the form of a Contest Winner Alert. Have you noticed that the email was sent from a strange email address? Also, you can notice some typos or misspelled words. This kind of email pressurizes you to respond promptly and with more information. The above is just an example of what a Phishing email looks like! Hence, always think before clicking if you don’t want to get tricked!
- Be cautious about website security
Before entering sensitive information on a website, ensure its security. It’s always advisable to look for a padlock icon in the address bar and that the URL begins with “https://” instead of “http://”. The “s” indicates a secure connection and you need to follow these two things.
Also, you can install Total Security Software as it protects your system from malicious websites and provides you with anti-phishing and anti-malware protection so that you don’t become another victim of a cyber-attack! In addition to HTTPS, you should ask yourself these 4 questions to enhance the Total Security of your website.
- Is it offering too good to be true deals?
- Do the links look spammy when I am hovering the mouse over the URL?
- Does the website look spammy or spooky?
- Is the website secured?
- Be careful about sensitive information requests
Legitimate organizations usually don’t ask for personal information, such as passwords or credit or Debit card details, or any kind of OTP via email or message. So, be careful before sharing. If you receive a link or a request for sharing your confidential information from a company or any organization, verify its identity to ensure authenticity. Call the company directly by taking the contact information from their original website and ask if the request is genuine or not!
- Create strong and hard-to-guess passwords
Ensure strong and unique passwords for all your online accounts. Avoid using common phrases or easily guessable information as hackers can easily guess them.
If your password is weak, hackers can easily guess it, making it easy for them to gain access to your account. Secure passwords are your first line of defense against unauthorized access to confidential information.
- Activate two-factor authentication (2FA)
Enabling two-factor authentication adds an extra layer of security by requiring a secondary form of verification, such as a temporary code sent to your mobile device, in addition to your password.
2FA significantly improves the security posture but doesn’t guarantee absolute protection. It is still essential to use strong and unique passwords, regularly update your software, and practice other Cybersecurity measures to maintain a robust defense against unauthorized access.
- Keep your Antivirus Software up-to-date
Regularly updating your Total Security Software is important if you want to stay away from Phishing Attacks. These updates often include patches for known vulnerabilities, protecting against potential attacks.
- Educate yourself and others
Keeping yourself informed about the latest phishing techniques and scams keeps you one step ahead. Also, you can share this knowledge with friends, family, and colleagues to help them stay safe from rising Phishing scams.
- Trust your instincts
If something seems suspicious, trust your instincts and exercise caution. If you receive an email or message that raises concerns, contact the organization directly through their official website or phone number. This will verify its authenticity.
To Conclude,
By following these 9 Tips and staying vigilant, you can significantly reduce the risk of falling victim to phishing attacks that have taken the world by their storm. Remember, “An ounce of prevention is worth a pound of care.” This quotation is especially true when it comes to protecting yourself from the rising Phishing Scams.
Installing Total Security Software in your system solves all your queries as it comes with Anti-Phishing & Anti-Malware protection that keeps you safe from phishing attacks and Malware respectively. Not only this, but it also gives you USB threat protection and helps you exercise parental control to keep a check on your kid’s online activities.
So, do you want to stay safe from the rising cyber-attacks?
If yes, Total Security is the best choice! Go! Try the Free Antivirus version, and experience a smooth internet journey!
Disclaimer:
The views expressed in the blog are of the blogger and do not necessarily represent or reflect the views written on the website.




